I would like to share with you a case I got that allowed me to explore the ASA, as I am no ASA expert I hope that is not to dumb and will provide some added value but if not then ok I will share it anyway
For the case study here lets say there is no network beside the diagram you will see bellow
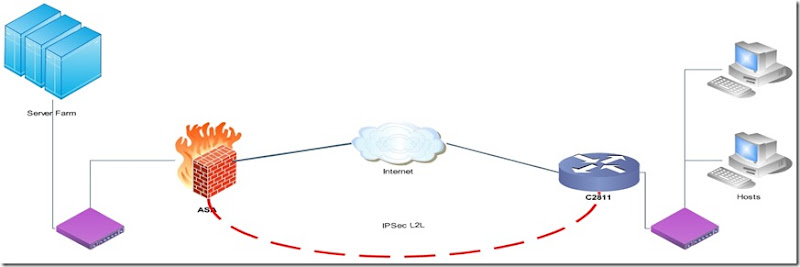
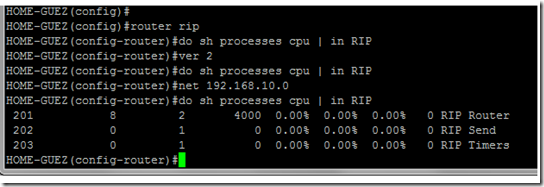
First I would like to share configuration and some debug commands (and there output).
###ASA
crypto isakmp enable <outside-if-name>
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 1
lifetime 86400
access-list IPSec-traffic extended permit ip <SOURCE_NET_SERVER_FARM> <DESTINATION_NET_HOSTS>
crypto ipsec transform-set TS esp-des esp-md5-hmac
crypto map IPSEC 10 match address IPSec-traffic
crypto map IPSEC 10 set peer <C2800-DST-IP>
crypto map IPSEC 10 set transform-set TS
crypto map IPSEC interface <outside-if-name>
tunnel-group <C2800-DST-IP> type ipsec-l2l
tunnel-group <C2800-DST-IP> ipsec-attributes
pre-shared-key <PASSWORD>
###ROUTER
#IKE PHASE 1
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key <PASSWORD> address 0.0.0.0 0.0.0.0
#IKE PHASE 2 IPSEC
crypto ipsec transform-set TS esp-des esp-md5-hmac
crypto dynamic-map DYN 10
set transform-set TS
crypto map IPSEC 10 ipsec-isakmp dynamic DYN
interface <X>
crypto map IPSEC
# ASA SOME SHOW/DEBUG COMMANDS
#
ciscoasa(config)# sh isakmp sa detail
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: <C2800-DST-IP>
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Encrypt : des Hash : MD5
Auth : preshared Lifetime: 86400
Lifetime Remaining: 57501
ciscoasa(config)# sh ipsec sa detail
interface: outside
Crypto map tag: IPSEC, seq num: 10, local addr: <ASA-SRC-IP>
access-list IPSec-traffic permit ip <SOURCE_NET_SERVER_FARM> <DESTINATION_NET_HOSTS>
local ident (addr/mask/prot/port): (SOURCE_NET/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (DESTINATION_NET/255.255.255.0/0/0)
current_peer: <C2800-DST-IP>
#pkts encaps: 71917, #pkts encrypt: 71917, #pkts digest: 71917
#pkts decaps: 71903, #pkts decrypt: 71903, #pkts verify: 71903
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 71917, #pkts comp failed: 0, #pkts decomp failed: 0
#pkts no sa (send): 0, #pkts invalid sa (rcv): 0
#pkts encaps failed (send): 0, #pkts decaps failed (rcv): 0
#pkts invalid prot (rcv): 0, #pkts verify failed: 0
#pkts invalid identity (rcv): 0, #pkts invalid len (rcv): 0
#pkts replay rollover (send): 0, #pkts replay rollover (rcv): 0
#pkts replay failed (rcv): 0
#pkts min mtu frag failed (send): 0, #pkts bad frag offset (rcv): 0
#pkts internal err (send): 0, #pkts internal err (rcv): 0
local crypto endpt.: <ASA-SRC-IP>, remote crypto endpt.: <C2800-DEST-IP>
path mtu 1500, ipsec overhead 58, media mtu 1500
current outbound spi: E1C2DB71
inbound esp sas:
spi: 0xE8F3372E (3908253486)
transform: esp-des esp-md5-hmac none
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 1, crypto-map: IPSEC
sa timing: remaining key lifetime (kB/sec): (4274983/1861)
IV size: 8 bytes
replay detection support: Y
outbound esp sas:
spi: 0xE1C2DB71 (3787643761)
transform: esp-des esp-md5-hmac none
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 1, crypto-map: IPSEC
sa timing: remaining key lifetime (kB/sec): (4274983/1861)
IV size: 8 bytes
replay detection support: Y
# ISAKMP DEBUG
ciscoasa# debug crypto isakmp
HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 192
%ASA-7-713236: IP = <C2800-DEST-IP>, IKE_DECODE RECEIVED Message (msgid=c49feb32) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 192
%ASA-7-715047: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, processing hash payload
%ASA-7-715047: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, processing SA payload
%ASA-7-715047: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, processing nonce payload
%ASA-7-715047: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, processing ID payload
%ASA-7-714011: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, ID_IPV4_ADDR_SUBNET ID received-SOURCE_NET_SERVER_FARM
%ASA-7-715047: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, processing ID payload
%ASA-7-714011: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, ID_IPV4_ADDR_SUBNET ID received--DESTINATION_NET_HOSTS
%ASA-7-715047: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, processing notify payload
%ASA-7-713906: Responder Lifetime decode follows (outb SPI[4]|attributes):
%ASA-7-713906: 0000: 37D453FB 80010001 00020004 00000E10 7.S.............
%ASA-5-713073: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, Responder forcing change of IPSec rekeying duration from 28800 to 3600 seconds
%ASA-7-713906: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, loading all IPSEC SAs
%ASA-7-715001: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, Generating Quick Mode Key!
%ASA-7-715001: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, Generating Quick Mode Key!
%ASA-6-602303: IPSEC: An outbound LAN-to-LAN SA (SPI= 0x37D453FB) between <ASA-SRC-IP> and <C2800-DEST-IP>(user= <C2800-DEST-IP>) has been created.
%ASA-5-713049: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, Security negotiation complete for LAN-to-LAN Group (<C2800-DEST-IP>) Initiator, Inbound SPI = 0x24d888f2, Outbound SPI = 0x37d453fb
%ASA-7-713906: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, oakley constructing final quick mode
%ASA-6-602303: IPSEC: An inbound LAN-to-LAN SA (SPI= 0x24D888F2) between <ASA-SRC-IP> and <C2800-DEST-IP> (user= <C2800-DEST-IP>) has been created.
%ASA-7-714006: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, IKE Initiator sending 3rd QM pkt: msg id = c49feb32
%ASA-7-713236: IP = <C2800-DEST-IP>, IKE_DECODE SENDING Message (msgid=c49feb32) with payloads : HDR + HASH (8) + NONE (0) total length : 72
%ASA-7-715007: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, IKE got a KEY_ADD msg for SA: SPI = 0x37d453fb
%ASA-7-715077: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, Pitcher: received KEY_UPDATE, spi 0x24d888f2
%ASA-6-713905: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, Starting P2 Rekey timer to expire in 3420 seconds
%ASA-5-713120: Group = <GRP-NAME>, IP = <C2800-DEST-IP>, PHASE 2 COMPLETED (msgid=c49feb32)
# IPSEC DEBUG
ciscoasa# debug crypto ipsec
%ASA-3-713119: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, PHASE 1 COMPLETED
%ASA-7-713121: IP = <C2800-DEST-IP>, Keep-alive type for this connection: DPD
%ASA-7-713906: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Starting phase 1 rekey timer: 82080000 (ms)
%ASA-7-715006: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, IKE got SPI from key engine: SPI = 0xeaa54840
%ASA-7-713906: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, oakley constucting quick mode
%ASA-7-715046: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, constructing blank hash payload
%ASA-7-715046: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, constructing IPSec SA payload
%ASA-7-715046: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, constructing IPSec nonce payload
%ASA-7-715001: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, constructing proxy ID
%ASA-7-713906: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Transmitting Proxy Id:
Local subnet: SOURCE_NET_SERVER_FARM mask 255.255.255.0 Protocol 0 Port 0
Remote subnet: DESTINATION_NET_HOSTS Mask 255.255.255.0 Protocol 0 Port 0
%ASA-7-714007: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, IKE Initiator sending Initial Contact
%ASA-7-715046: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, constructing qm hash payload
%ASA-7-714004: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, IKE Initiator sending 1st QM pkt: msg id = 0b0b91e2
%ASA-7-713236: IP = <C2800-DEST-IP>, IKE_DECODE SENDING Message (msgid=b0b91e2) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 192
%ASA-7-713236: IP = <C2800-DEST-IP>, IKE_DECODE RECEIVED Message (msgid=b0b91e2) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 192
%ASA-7-715047: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, processing hash payload
%ASA-7-715047: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, processing SA payload
%ASA-7-715047: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, processing nonce payload
%ASA-7-715047: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, processing ID payload
%ASA-7-714011: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, ID_IPV4_ADDR_SUBNET ID received--SOURCE_NET_SERVER_FARM
%ASA-7-715047: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, processing ID payload
%ASA-7-714011: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, ID_IPV4_ADDR_SUBNET ID received--DESTINATION_NET_HOSTS
%ASA-7-715047: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, processing notify payload
%ASA-7-713906: Responder Lifetime decode follows (outb SPI[4]|attributes):
%ASA-7-713906: 0000: 18C33FE5 80010001 00020004 00000E10 ..?.............
%ASA-5-713073: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Responder forcing change of IPSec rekeying duration from 28800 to 3600 seconds
%ASA-7-713906: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, loading all IPSEC SAs
%ASA-7-715001: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Generating Quick Mode Key!
%ASA-7-715001: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Generating Quick Mode Key!
%ASA-6-602303: IPSEC: An outbound LAN-to-LAN SA (SPI= 0x18C33FE5) between <ASA-SRC-IP> and <C2800-DEST-IP> (user= <C2800-DEST-IP>) has been created.
%ASA-5-713049: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Security negotiation complete for LAN-to-LAN Group (<C2800-DEST-IP>) Initiator, Inbound SPI = 0xeaa54840, Outbound SPI = 0x18c33fe5
%ASA-7-713906: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, oakley constructing final quick mode
%ASA-6-602303: IPSEC: An inbound LAN-to-LAN SA (SPI= 0xEAA54840) between <ASA-SRC-IP> and <C2800-DEST-IP> (user= <C2800-DEST-IP>) has been created.
%ASA-7-714006: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, IKE Initiator sending 3rd QM pkt: msg id = 0b0b91e2
%ASA-7-713236: IP = <C2800-DEST-IP>, IKE_DECODE SENDING Message (msgid=b0b91e2) with payloads : HDR + HASH (8) + NONE (0) total length : 72
%ASA-7-715007: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, IKE got a KEY_ADD msg for SA: SPI = 0x18c33fe5
%ASA-7-715077: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Pitcher: received KEY_UPDATE, spi 0xeaa54840
%ASA-6-713905: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, Starting P2 Rekey timer to expire in 3420 seconds
%ASA-5-713120: Group = <C2800-DEST-IP>, IP = <C2800-DEST-IP>, PHASE 2 COMPLETED (msgid=0b0b91e2)
THERE WILL BE CONTINUE…